Outsmart Sophisticated Scams: How to Use Email Tracing as Digital Self-Defense

In today’s digital landscape, your inbox is a battlefield. Every day, scammers deploy increasingly sophisticated attacks designed to steal your data, compromise your systems or drain your bank account.
That’s why learning to trace email origins isn’t just a neat trick—it’s an essential skill for your digital self-defense arsenal.
This guide will show you how to trace emails to the real sender and identify what emails look like that make this a necessity.
The Threat Landscape: Common Email Scams for Businesses
Gone are the days of easily spotted scams. Today’s cyber criminals craft messages that look eerily legitimate:
Fake shipping notices urging you to click links or download attachments.
Alarming messages about your domain or hosting account requiring immediate action.
Requests to “confirm” account details for services you may actually use.
Seemingly legitimate bills or payment notifications from trusted vendors.
The end game? Either installing malware on your system or tricking you into handing over sensitive information.
Why Email Tracing Matters
Knowing how to trace an email’s true origin gives you a powerful edge:
How Email Tracing Works
Every email contains a hidden message within it called the header. This header stores information about the email’s journey, including:
- Sender’s IP Address: While the sender’s email address might be fake, the IP address can provide clues about the origin’s location.
- Server Hops: The email travels through various mail servers before reaching you. The header shows the trail of servers it passed through.
- Timestamps: These timestamps reveal when the email interacted with each server, giving a timeline of its journey.

Unearthing the Email’s Path
To trace an email, you’ll need to access its header. The process for finding the header varies depending on your email provider.
For example, here’s how to access the email header in Gmail and take your first steps toward uncovering the email’s source:
1. Open the email you want to trace in your Gmail account. Click the three dots (…) located in the top right corner of the email. Select “Show original” from the dropdown menu:
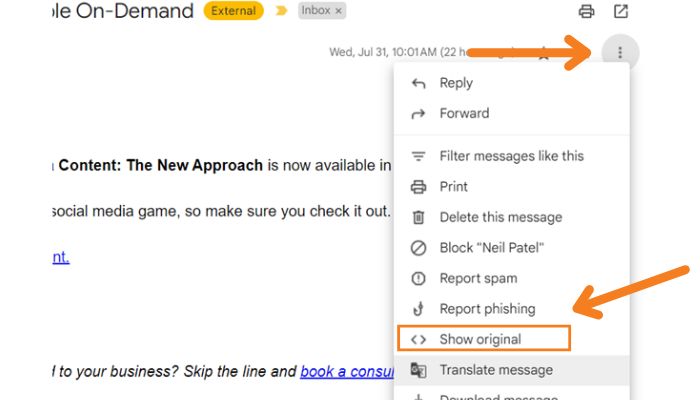
2. A new window will display the email’s full header. Look for the “Received” lines in the header. These show the path the email took.
If you have a different email provider, a quick web search for “view email header in [your email provider]” will guide you through the steps.
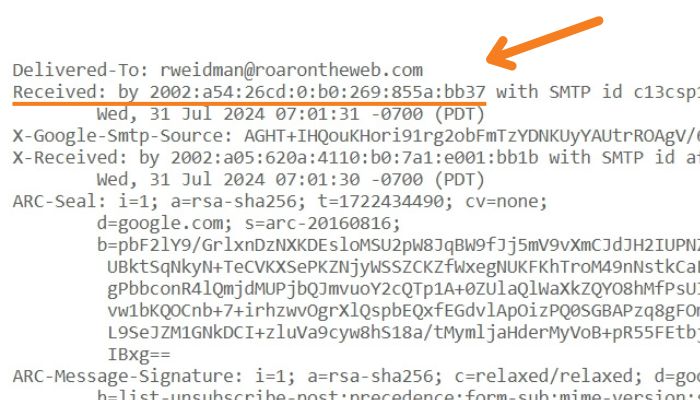
3. Find the originating IP address, usually in the last “Received” line:
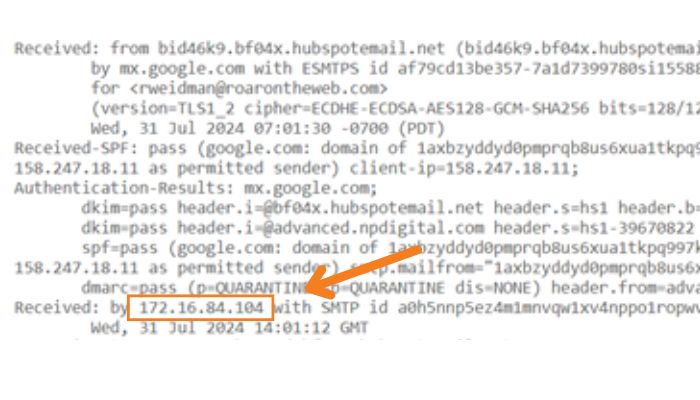
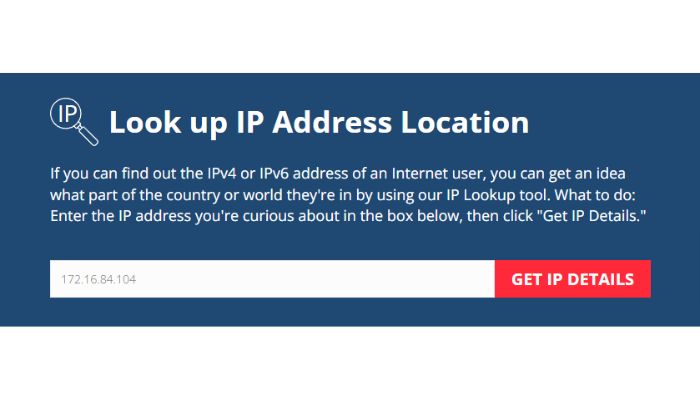
4. Use online tools like free IP lookup services such as whatismyipaddress.com to get more information about the IP address:
Remember that email tracing has limitations. VPNs, proxy servers and other technologies can obscure an email’s true origin.
If the email is legitimate, the chances are high the IP address will match an IP from that company. If it is not legitimate, the bad guys will probably have concealed or obfuscated the owner of that IP address.

Red Flags to Watch For
When examining an email header, keep an eye out for these telltale signs of potential fraud:
- Mismatched Domains: The visible “From” address doesn’t match the actual sending domain in the header.
- Unexpected Server Hops: The email took an unusual route through unfamiliar or suspicious servers.
- Failed Authentication: If SPF, DKIM or DMARC checks failed, be extra cautious.
Verifying Email Legitimacy Beyond Gmail
The techniques mentioned so far primarily focus on Gmail. However, email tracing principles apply to emails from any source, including social media platforms like Facebook. Here’s how to confirm if an email claiming to be from Facebook is legitimate:
- Check the Sender’s Email Address: Legitimate Facebook emails will always originate from an address ending in “@facebookmail.com”.
- Review Recent Facebook Emails: Facebook provides a list of recent emails they’ve sent you within your Security and Login Settings. This allows you to compare the suspicious email with verified communication from Facebook.
Here’s how to access the list of recent Facebook emails:
- Go to your Facebook profile and click the dropdown arrow in the top right corner
- Select “Settings & Privacy” followed by “Settings”
- Click on “Accounts Center” and then “Password and Security”
- Under “Security Checks,” you’ll find “Recent emails”
Remember, a little email detective work can go a long way in protecting yourself from online scams and ensuring your own emails reach their intended destination.


Look Out for This New Technique
A homograph attack, also known as IDN spoofing, occurs when an attacker registers a domain name that closely resembles a legitimate one but uses characters from different scripts that look similar to Latin letters.
For example, an attacker might use the Cyrillic letter “а” instead of the Latin “a,” creating a domain like “аррle.com” that visually mimics “apple.com.” This tactic exploits the fact that users may not notice the subtle differences, leading them to mistakenly trust the fake site.
To facilitate this deception, attackers use Punycode, a method that encodes internationalized domain names (IDNs) containing non-Latin characters into a format compatible with the Domain Name System (DNS).
For instance, the Punycode representation of “аррle.com” would appear as “xn--80ak6aa92e.com.” When users encounter such domains, they may inadvertently click on links that direct them to phishing sites, risking their personal information and security.
Overall, homograph attacks leverage the visual similarities between characters from different scripts to create deceptive domain names, making it essential for you to be vigilant and discerning when navigating the web.
Frequently Asked Questions
You can trace it to the public computer’s IP address, but identifying the specific sender may be difficult.
It can be quite accurate, but sophisticated users can mask their true location.
Report it to your email provider and consider contacting law enforcement if the content is threatening or illegal.
